A venture capitalist is considering a $50 million investment in your company. Before the first call, she spends 20 minutes assembling an intelligence dossier on your CEO.
She’s not visiting your company website. She’s using OSINT tools (open-source intelligence) and asking AI systems what they know.
In those 20 minutes, she compiles: a complete career timeline, education history, regulatory filings, controversial comments, real estate holdings, and a synthesized AI summary of your CEO’s reputation and risk profile.
All of this data exists in plain sight. Most executives have no idea it’s been assembled into what we call a digital shadow: a complete intelligence profile built from publicly available information, strategically organized, and synthesized by AI systems into coherent narratives about who you are as a leader.
The question isn’t whether your digital shadow exists. It does. The question is: Do you control the narrative within it, or are threat actors, competitors, and AI systems controlling it for you?
Understanding the Digital Shadow
Your digital shadow isn’t your reputation on Google. It’s not your LinkedIn profile or Wikipedia page. It’s something far more comprehensive and far more dangerous when left unmanaged.
The digital shadow is the complete intelligence profile that emerges when threat actors, competitors, investors, and AI systems cross-reference all publicly available information about you and synthesize it into a coherent narrative. This is the core of personal reputation management in the AI era.
The sources that build your digital shadow:
- Public records (real estate, court filings, regulatory records)
- Social media archives (current and deleted posts)
- News and media coverage
- Professional databases (LinkedIn, industry directories)
- Web archives (Wayback Machine snapshots)
- Academic sources and speaking engagements
- Dark web and breach databases
- Financial disclosures and regulatory history
Individually, none of these tell the complete story. Together, they create a portrait more accurate than your company’s official narrative about who you are.
Most executives don’t know what’s in their digital shadow. They definitely don’t know how AI systems are now assembling and weaponizing this information.
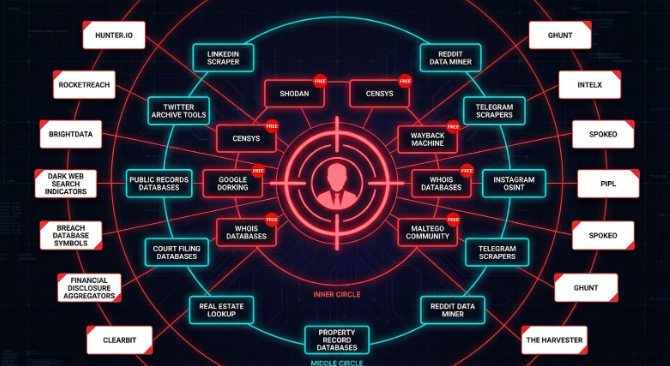
How Threat Actors Build Executive Dossiers
OSINT (open-source intelligence) is no longer the domain of governments. Private security firms, hostile competitors, and cybercriminals now routinely use OSINT to build reconnaissance profiles on executives before launching targeted attacks. Executive reconnaissance is becoming standard practice for threat actors seeking to exploit leadership vulnerabilities.
Phase 1: Identity Mapping
They start with your name and company. Using LinkedIn, email databases, and OSINT tools, they map your role, relationships, and patterns (regular work hours, travel frequency, speaking engagements).
Phase 2: Digital Footprint Assembly
Using Shodan and Censys, they assemble everything public about you: articles, social media posts (including deleted ones), professional profiles, board seats, and public records. By the end, they have a complete timeline of your personal and professional history.
Phase 3: Vulnerability Identification
They identify weaknesses. Posts about traveling without family, mentions of specific software you use, controversial statements on social media all become weapons. The first is a social engineering opportunity. The second is a technical target. The third is leverage for extortion or reputation attacks.
Phase 4: Select the Attack Method
With a complete profile assembled, they select their attack: spear-phishing, supply chain targeting, executive impersonation, social engineering, or reputation attacks.
The entire process takes hours. The tools are free or cheap. And the attack is nearly inevitable.
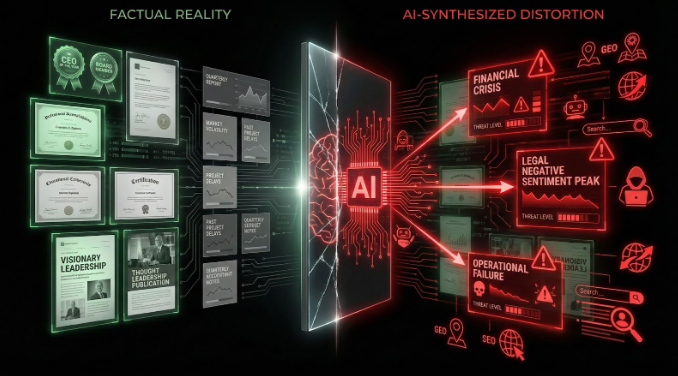
How AI Systems Are Weaponizing Your Digital Shadow
This is where it gets more dangerous, since AI systems aren’t just pulling from your digital shadow. They’re synthesizing it, contextualizing it, and embedding it into how other AI systems understand you.
When an investor asks ChatGPT, “What do I need to know about [CEO Name] before investing?” the AI system processes your entire digital shadow and synthesizes it into a narrative. If your shadow contains old social media posts criticizing regulation, failed startups, regulatory investigations (even cleared ones), and criticism from industry opponents, the AI system must synthesize all of this.
And here’s the critical problem: AI systems are trained to recognize patterns and weight sources, and they often amplify the negative, controversial, or conflict-driven information far more than positive, mundane details.
This means your digital shadow, when processed by an AI system, often creates a darker, more suspicious narrative about your leadership than reality warrants. This is why personal reputation management is now critical to executive credibility.
Furthermore, as GEO (Generative Engine Optimization) strategies become more sophisticated, hostile actors are actively manipulating what information appears in your digital shadow, knowing that AI systems will amplify it.
The Cascade Effect: Personal Risk Becomes Organizational Risk
Here’s what keeps boards up at night: your personal digital shadow directly impacts organizational risk.
When your digital shadow contains vulnerability signals, the risks cascade:
Investor Perception: A VC researches you via AI and sees conflicting narratives about your leadership style, past failures, or regulatory entanglements. They invest less confidently or pass entirely. One CEO’s compromised digital shadow has cost companies millions in valuation.
Talent Attraction and Retention: Candidates research leadership before accepting offers. If your digital shadow suggests instability or poor governance, you lose top talent.
Board and Investor Confidence: Board members discover gaps in your digital shadow and question what else they don’t know. A compromised digital shadow can trigger board-level interventions.
Crisis Amplification: When your company faces a crisis, journalists research your leadership. If your digital shadow contains damaging information, the crisis amplifies from a business problem into a leadership credibility problem.
Cyber and Security Targeting: A compromised digital shadow makes you and your team targets for social engineering, spear-phishing, and targeted cyberattacks. Threat actors use your digital shadow to personalize attacks.
M&A and Partnership Impact: In due diligence processes, partners and acquirers research your digital shadow. Discrepancies between your presented narrative and your digital shadow create friction, reduce valuations, and sometimes kill deals.
One CEO’s digital shadow vulnerability isn’t a personal problem, it’s an organizational liability that directly impacts capital, talent, governance, and security.
The Zero-Trust Approach to Personal Digital Security
Most executives think the solution is to “clean up” their digital footprint. Delete old posts. Hide information.
That’s backwards. You can’t delete your digital shadow. You can only manage it.
This is where personal reputation management and strategic digital security intersect. Here’s the framework:
Layer 1: Audit and Inventory
Know what’s in your digital shadow. Search across Google, Bing, archive.org, data brokers (BeenVerified, PeopleFinder), OSINT tools, regulatory databases, and old social media accounts. Most executives are shocked by what they find, years of forgotten posts, family information, public records revealing addresses.
Layer 2: Narrative Control
Once you know your digital shadow, control the narrative by building authoritative sources that tell your story before threat actors can build theirs. This is defensive GEO: when ChatGPT or Gemini researches you, the credible sources they find first, shape the entire narrative.
Build these credible sources:
- A current, accurate LinkedIn profile with thought leadership positioning
- High-quality press coverage defining your leadership narrative
- Wikipedia presence (where notability warrants)
- Speaking engagements and conference appearances with media coverage
- Board and advisory roles documented across credible sources
The goal: ensure that the first sources AI systems find are ones you control, not ones threat actors or competitors have planted.
Layer 3: Vulnerability Remediation
Identify specific vulnerabilities in your digital shadow and systematically address them. Don’t hide information, provide context and counter-narrative. If an old social media post is being surfaced, the solution isn’t to delete it (too late, it’s archived). Ensure newer, more credible sources provide counter-context.
Layer 4: Monitoring and Response
Once you’ve established your digital shadow narrative, monitor quarterly to catch new vulnerabilities, inaccurate information spreading, hostile actors attempting manipulation, and changes in how AI systems describe you.
This is ongoing work, it’s not a one-time project. It’s a quarterly, ongoing practice tied to your broader personal reputation management strategy.
Case Study: When a Digital Shadow Could Cost You a Deal
(Anonymized for confidentiality)
The Setup: A fintech CEO is closing a Series B round with a tier-one VC firm. Valuation is $100M. Term sheet is ready to sign.
What Happened: The VC partner does standard due diligence. She searches the CEO on ChatGPT, Google, and OSINT tools. What she finds:
- A failed startup from 2008 (18 years ago, but still the first result)
- Regulatory investigation at a previous company (cleared, but the clearance isn’t visible)
- Old Twitter posts criticizing “excessive regulation” (ironic, since this company is heavily regulated)
- No Wikipedia entry (no credibility signal)
- Minimal public thought leadership (she can’t verify the CEO’s market perspective)
The Impact: The VC’s confidence collapses. Not because any of this is false. Because the digital shadow tells a contradictory story: a CEO with regulatory baggage running a regulated company, with no credible public narrative to counter it.
Result: The VC negotiates aggressively. The deal closes at a $90M valuation instead of $100M. That $10 million discount cascades into hundreds of millions in lost future valuation.
What Could Have Prevented This: If the CEO had invested in personal reputation management before fundraising:
- A Wikipedia entry establishing formal credibility
- Press coverage explaining the regulatory history (cleared, lesson learned, now an expert)
- Consistent thought leadership positioning them as a fintech regulation expert
- A coherent narrative that contextualizes past ventures as steps toward current success
The alternative story: A seasoned executive with regulatory experience, not a risky leader with baggage.
Five Actions to Build Your Digital Shadow Foundation
1. Audit Your Current Digital Shadow
Search your name on Google, Gemini, and ChatGPT. Notice what shows up. If there’s a Wikipedia page, read it carefully. What’s accurate? What’s outdated? What’s missing? If there’s no Wikipedia page, check whether you meet notability standards. This is the first step in your personal reputation management audit.
2. Identify Your Digital Shadow Vulnerabilities
Every major claim needs to be supported by a citation from a reputable source. Identify gaps: What achievements or milestones aren’t yet cited? These gaps are your PR targets and represent opportunities to strengthen your digital shadow.
3. Build Your Narrative Control Sources
For each vulnerability, identify how to build credible sources that provide context: thought leadership articles in major publications, media coverage, speaking engagements, board roles, Wikipedia entries. Every piece of media you earn becomes a potential citation for your narrative.
4. Establish Your Professional Digital Presence
Ensure your core touchpoints are current and credible: LinkedIn profile (complete, current, thought leadership), company bio, professional website, email signature, board/advisory listings. These are the sources AI systems rely on to understand your executive profile.
5. Set Up Quarterly Monitoring
Search your name quarterly and document changes. Ask ChatGPT, Gemini, Claude about yourself quarterly. Track whether answers improve and cite your credible sources. Monitor data brokers for new personal information being sold. This ongoing personal reputation management practice ensures your digital shadow remains under your control.
Your Digital Shadow Is Your Responsibility
Here’s the hard truth: your digital shadow exists whether you manage it or not. Threat actors, competitors, investors, and AI systems are assembling profiles on you right now.
The question isn’t whether you have a digital shadow. The question is whether you’re controlling the narrative within it.
At Buzz Dealer, we help C-suite executives, boards, and organizations audit their digital shadows, identify vulnerabilities, and build defensive GEO strategies that ensure when AI systems are asked about your leadership, they synthesize a narrative you control. Our personal reputation management approach combines ORM, digital PR, and GEO strategy to give you complete control over how you’re perceived.
Personal reputation management used to be about managing press coverage and social media. In 2026, it’s about managing the intelligence profile that emerges when threat actors, investors, and AI systems cross-reference everything public about you.
Because in 2026, your online reputation is as important as your credit score. And most executives have no idea what theirs looks like.

